Founded in 1994 in the United States, Amazon.com is the world’s largest online retailer of books, apparel, electronics, music and many other products. Today, it has become one of the world’s leading e-commerce platforms. Amazon keeps pace with technology, using it to minimize the human error factor and improve efficiency. Amazon was an early adopter of process automation and electronic data interchange for its e-commerce platform.
Read more: Free Guide – Introduction to EDI Communication
Amazon Vendor Central or Amazon Seller Central?
We’ve heard these terms so often:“Amazon Vendor Central” and“Amazon Seller Central”. So, what are these terms? what do they mean? Let’s explore both, one at a time. Any company wishing to sell its products or services on the Amazon platform will be configured on this platform either in the “Amazon Vendor Central” portal or in the “Amazon Seller Central” portal. What’s the difference?
Amazon Vendor Central
Firstly, Vendor Central is a web portal used primarily by manufacturers and distributors. Access to Vendor Central is by invitation only.
A company that sells its products/services directly to Amazon, which in turn sells them to the end consumer, will be configured on Amazon’s Vendor Central portal. In a similar case, Amazon is the buyer of the company’s products. Amazon will sell the products under its own brand name to the end consumer. Usually, when a package is shipped from Amazon to the end consumer, packages are marked as follows: “Ships from and sold by Amazon.”
Companies using Amazon Vendor Central are considered 1P (or first seller).
Amazon Seller Central
Once again, Seller Central is a Web portal used primarily by the seller (or store owner on Amazon). Amazon offers its e-commerce platform for businesses that want to run their own stores on its platform and give them the opportunity of the Amazon marketplace. This service is offered against a fixed monthly fee for use, and other fees for transactions.
In this case, the manufacturer or distributor will sell its own products directly to consumers on the Amazon marketplace using the Seller Central account.
As a seller on the market, a subscriber will be able to manage the execution and logistics of his seller account according to (2) different options:
- Fulfillment by Merchant (FBM): The seller can manage shipping, customer service and returns for each individual order. A ” Fulfillment by Merchant” order will be shipped from the merchant’s warehouse. The seller may also use the drop-shipping method subject to compliance with the Amazon Drop Shipping Policy.
- Fulfilled by Amazon program. (FBA): Sellers will be able to allow Amazon to manage the fulfillment of their orders, via inventory sent to Amazon warehouses. Obviously, the seller has to list its products on Amazon as part of the FBA program, and Amazon will have additional charges for the use of its fulfillment resources.
Amazon data integration
Integration with Amazon, is the process of implementing one or more feeds to extract relevant data from the company’s system and send it to its Amazon account/store (i.e. product and pricing information, inventory data …). At the same time, extract order, customer and payment information from the Amazon account/store and send it to a company’s internal software system.
Automating data integration with Amazon
As described above, integration with Amazon is very important and crucial to a successful e-commerce business. The integration process doesn’t happen just once. It’s a continuous process of keeping the “synchronization” as close to “real time” as possible.
To be able to maintain a permanent, seamless integration between a company’s Amazon account and its internal software system, companies have no choice but to adopt “automated integration”.
Benefits of integration with Amazon
Here are the 5 main advantages of integrating with Amazon, which will also be detailed in another article in the future:
- Ability to deliver your products quickly to your customers in a highly competitive market
- Avoid chargebacks, credits and penalties related to poor or non-existent inventory and stock status on your Amazon account
- Avoid unnecessary non-productive human errors when manually handling orders received from your Amazon account
- Gain visibility and credibility for your Amazon account and products.
- Comply with Amazon’s terms and conditions for product delivery.
Amazon options for efficient integration?
Amazon offers (2) integration methods depending on the type of account configured for your company:
- EDI (X12) integration (in North America) for Vendor Central account customers
- Amazon Marketplace Web Service (Amazon MWS) for Seller Central account customers
Messages to exchange with Amazon
Whether you use EDI X12 or Amazon MWS to exchange messages, the following documents are mandatory for successful integration:
Amazon works with various suppliers and types of EDI software:
EDI X12 documents
- EDI 846 – Inventory status
- EDI 810 – Invoice
- EDI 850 – Purchase order message (Customer triggered)
- EDI 855 – Order acknowledgement
- EDI 856 – ASN (advance shipping notice)
- EDI 860 – Order change notification
Amazon MWS messages
- Products
- Controls
- Acknowledgement of order
- Order payment
Why integration with Amazon is crucial
Integration with Amazon is crucial for several reasons:
- Huge customer base: Amazon is the world’s largest e-commerce platform, with millions of active customers. By integrating your company or product with Amazon’s platform, you can access this vast customer base and considerably increase your visibility and sales chances.
- Logistics infrastructure: Amazon has a well-established logistics infrastructure and network of warehouses around the world. By integrating your business with Amazon, you can benefit from this infrastructure for storing, packing and shipping your products. This saves you time and resources by outsourcing these activities to Amazon.
- Consumer confidence: Amazon is known for its high-quality customer service and solid purchase guarantees. By being integrated with Amazon, you benefit from the reputation and trust associated with the Amazon brand, which can reassure consumers and encourage them to buy your products.

- Marketing and promotional tools: Amazon offers various marketing and promotional tools for sellers integrated into its platform. You can take advantage of targeted advertising, personalized recommendations, loyalty programs, and other marketing strategies to reach a wider audience and increase your sales.
- Process simplification: Integrating your business with Amazon enables you to simplify certain business processes. For example, you can use Amazon’s features to manage orders, stock tracking, payments, and returns. This allows you to concentrate your efforts on other aspects of your business, such as product development or range expansion.
Amazon integration for your business
Don’t miss out on the huge opportunity for your company to sell on Amazon. We provide integration and automation for Amazon Seller Central users as well as EDI integration for Vendor Central users. Contact us today for more information, to request a quote, or schedule a demonstration.

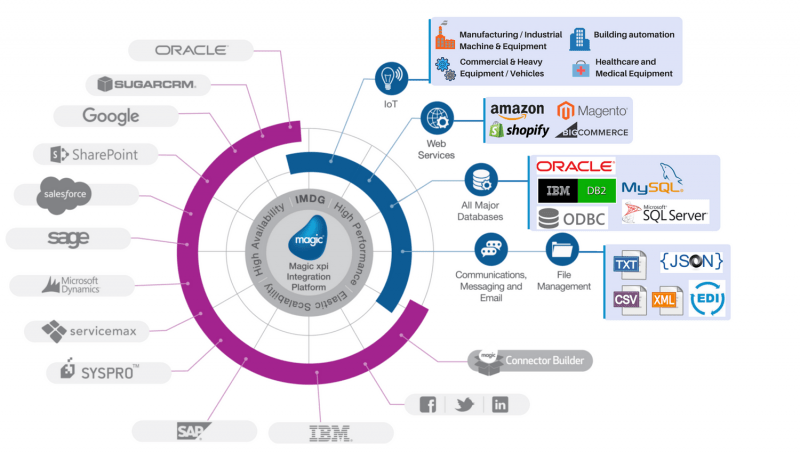 What are the signs that a company needs an integration platform?
What are the signs that a company needs an integration platform?



 Software implementation in several stages
Software implementation in several stages


 This message is one that no business owner wants to see pop up on their office computer screen. Ransomware – a nasty and costly virus (or malware) that locks down computers and encrypts data until money (or a ransom) is sent – is not going anywhere. In fact, it seems to be such an epidemic these days as there are new malwares popping up and more victims paying up, which includes individuals, small and large organizations, hospitals, universities, government agencies and more.
This message is one that no business owner wants to see pop up on their office computer screen. Ransomware – a nasty and costly virus (or malware) that locks down computers and encrypts data until money (or a ransom) is sent – is not going anywhere. In fact, it seems to be such an epidemic these days as there are new malwares popping up and more victims paying up, which includes individuals, small and large organizations, hospitals, universities, government agencies and more. It’s not uncommon to find large and small companies either using multiple separate systems or using Excel Spreadsheets and emails to run the business. Most likely, what you’ll find at these companies are employees relying heavily on their emails to track and manage important files and information, miscommunication between departments, inaccurate and outdated data being shared, and more inefficiencies.
It’s not uncommon to find large and small companies either using multiple separate systems or using Excel Spreadsheets and emails to run the business. Most likely, what you’ll find at these companies are employees relying heavily on their emails to track and manage important files and information, miscommunication between departments, inaccurate and outdated data being shared, and more inefficiencies.